
26 Aug Understanding the Importance of Chain of Custody
Chain of custody stands as the backbone of reliable evidence, scientific sample tracking, and even data security for countless organisations. Yet few realise just how extensively it shapes everyday business operations. In fact, sectors like pharmaceuticals and digital forensics rely on chain of custody procedures to maintain compliance and reduce legal risks, with precise timestamps logging every single transfer. Most think chain of custody is just a legal formality but its impact spans far wider and unlocks surprising advantages that most companies overlook.
Table of Contents
- Defining Chain Of Custody: Meaning And Scope
- Significance Of Chain Of Custody In Business Operations
- How Chain Of Custody Works: Principles And Practices
- Key Concepts Related To Chain Of Custody: Integrity And Accountability
- Real-World Applications And Challenges Of Chain Of Custody
Quick Summary
| Takeaway | Explanation |
|---|---|
| Maintain meticulous documentation | Accurate records are crucial for ensuring the integrity of evidence and compliance across industries. |
| Implement robust tracking mechanisms | Advanced tracking systems reduce human error and improve accountability for materials and information. |
| Ensure secure handling and transport | Controlled transfer environments safeguard against tampering, preserving the original state of items. |
| Utilise technology for efficiency | Embrace digital solutions like blockchain for real-time tracking and comprehensive audit trails. |
| Promote integrity and accountability | Foster a culture where every interaction is documented, ensuring transparency and trustworthiness in processes. |
Defining Chain of Custody: Meaning and Scope
Chain of custody represents a critically important documentation and tracking process that establishes the movement, handling, and transfer of evidence, items, or materials through a carefully documented sequence. This systematic approach ensures the integrity, security, and traceability of items from their initial collection through to final disposition.
Understanding the Core Concept
At its fundamental level, chain of custody is a comprehensive record-keeping mechanism designed to document every interaction, transfer, and transformation an item undergoes. Forensic Science International defines it as a meticulous process that tracks the progression of physical or digital evidence through various stages of handling.
Key characteristics of an effective chain of custody include:
- Chronological Documentation: Recording precise timestamps of every transfer
- Identification of Handlers: Noting each individual who interacts with the item
- Secure Transportation: Ensuring controlled and verifiable movement between authorized personnel
Practical Applications and Significance
The importance of chain of custody extends across multiple professional domains, including legal proceedings, scientific research, healthcare, and digital forensics. In legal contexts, maintaining an unbroken chain of custody is paramount for ensuring the admissibility of evidence in court. Any break or inconsistency in documentation could potentially compromise the entire investigative process.
Beyond legal realms, chain of custody plays a crucial role in sectors requiring strict accountability and traceability. Medical laboratories, pharmaceutical companies, and environmental research institutions rely on these protocols to maintain the reliability and authenticity of their collected specimens and research materials.
The systematic approach of chain of custody not only provides a transparent record but also serves as a critical safeguard against potential tampering, contamination, or unauthorized modifications. By implementing rigorous tracking mechanisms, organisations can demonstrate their commitment to maintaining the highest standards of professional integrity and scientific precision.

Significance of Chain of Custody in Business Operations
In the contemporary business landscape, chain of custody has emerged as a critical mechanism for ensuring transparency, accountability, and regulatory compliance across diverse industries. The systematic tracking and documentation of items, data, and processes serve as a fundamental protection strategy for organisations seeking to maintain operational integrity and mitigate potential risks.
Risk Management and Compliance
Businesses increasingly recognise chain of custody as an essential risk management tool. Deloitte’s Risk Management Research highlights that robust documentation processes can significantly reduce potential legal and financial vulnerabilities. By meticulously recording every transaction, transfer, and interaction, companies create an auditable trail that demonstrates due diligence and responsible management.
Key risk management benefits include:
- Legal Protection: Establishing clear evidence of proper handling
- Regulatory Compliance: Meeting industry-specific documentation requirements
- Fraud Prevention: Creating transparent tracking mechanisms
Financial and Operational Implications
The implementation of comprehensive chain of custody protocols extends far beyond mere documentation. It represents a strategic approach to protecting organisational assets, intellectual property, and sensitive information. In sectors such as supply chain management, manufacturing, and technology, these protocols become instrumental in verifying product authenticity, tracking inventory movements, and ensuring quality control.
Industrial sectors like pharmaceuticals, electronics, and advanced manufacturing rely heavily on precise chain of custody procedures to validate the origin, handling, and transformation of materials. This approach not only safeguards against potential counterfeiting but also provides granular insights into operational efficiency and potential areas of improvement.
Moreover, in an era of increasing digital transformation, chain of custody has expanded beyond physical items to encompass data management. Organisations must now track digital assets with the same rigour as physical products, ensuring data integrity, preventing unauthorized access, and maintaining comprehensive audit trails for cybersecurity and compliance purposes.
How Chain of Custody Works: Principles and Practices
Chain of custody operates through a systematic approach that meticulously documents and tracks the movement, handling, and transfer of items or information. This complex process involves multiple strategic components designed to maintain absolute integrity and accountability throughout an item’s lifecycle.
Documentation and Tracking Mechanisms
At the core of chain of custody are comprehensive documentation protocols that capture every single interaction and movement. National Institute of Standards and Technology emphasises the critical importance of creating a detailed, uninterrupted record that provides conclusive evidence of an item’s journey.
Key documentation requirements include:
- Precise Timestamps: Recording exact date and time of each transfer
- Individual Identification: Logging complete details of each handler
- Detailed Transfer Logs: Capturing method, location, and conditions of transfer
Verification and Authentication Processes
The verification stage represents a crucial checkpoint in maintaining chain of custody. Organisations implement multiple authentication mechanisms to ensure the reliability and integrity of tracked items. These processes typically involve creating unique identifiers, implementing secure handover protocols, and utilising advanced tracking technologies.
Verification methods might include digital signatures, tamper-evident seals, specialised tracking software, and rigorous cross-referencing procedures. By establishing multiple layers of authentication, organisations can create an almost impenetrable system of accountability that minimises the potential for unauthorized alterations or unrecorded interactions.
Moreover, modern chain of custody practices increasingly leverage technological solutions such as blockchain, advanced encryption, and real-time tracking systems. These innovations provide unprecedented levels of transparency and security, allowing organisations to maintain comprehensive records with minimal human intervention and maximum reliability.
Key Concepts Related to Chain of Custody: Integrity and Accountability
Integrity and accountability form the foundational principles underlying chain of custody, representing critical mechanisms that ensure the reliability, authenticity, and legal defensibility of tracked materials or information. These interconnected concepts go beyond simple record-keeping, embodying a comprehensive approach to maintaining the highest standards of professional conduct and systematic documentation.
Conceptual Foundations of Integrity
Integrity within chain of custody refers to the preservation of an item’s original condition and characteristics throughout its entire lifecycle. National Criminal Justice Reference Service emphasises that maintaining absolute integrity requires preventing any potential contamination, alteration, or unauthorized modification that could compromise the item’s original state.
Critical aspects of maintaining integrity include:
- Controlled Access: Limiting interactions to authorised personnel
- Secure Storage: Implementing protective environments
- Detailed Documentation: Recording every interaction comprehensively
Accountability and Transparency Mechanisms
Accountability in chain of custody extends beyond individual responsibility to create a systematic framework of transparent, verifiable interactions. This approach ensures that every person handling an item can be precisely identified, with their specific actions documented and traceable. Such mechanisms create a comprehensive audit trail that enables retrospective examination and validation of all processes.
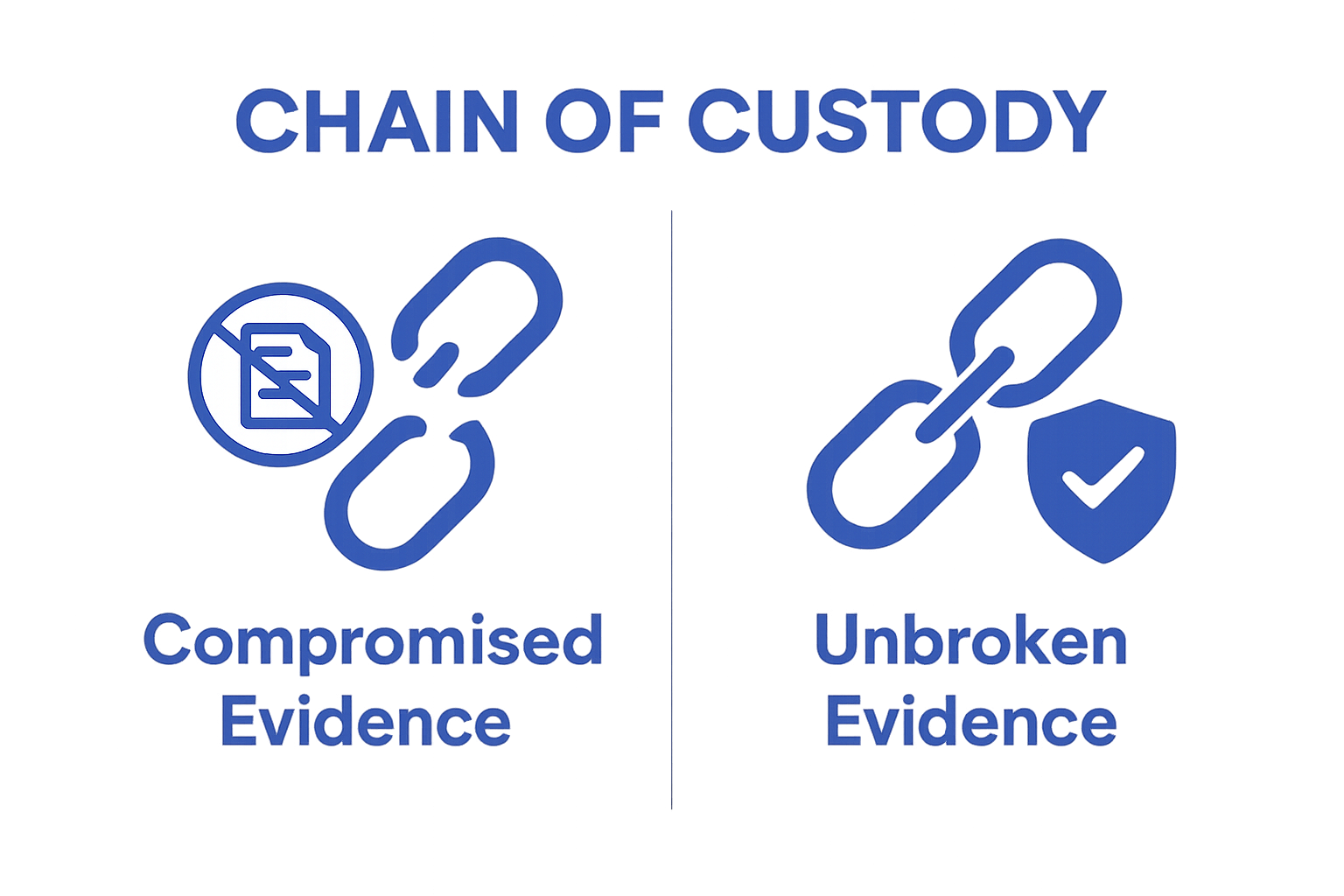
Organisations achieve accountability through strategies like establishing clear protocols, implementing robust tracking systems, and creating multiple verification checkpoints. These approaches transform accountability from a theoretical concept into a practical, enforceable standard that protects both the organisation and the integrity of the tracked items.
Ultimately, the intersection of integrity and accountability represents a sophisticated approach to managing complex informational and material assets. By embedding these principles into organisational practices, businesses can create resilient, transparent systems that withstand rigorous scrutiny and maintain the highest standards of professional excellence.
Real-world Applications and Challenges of Chain of Custody
Chain of custody extends far beyond theoretical frameworks, playing a crucial role in multiple professional domains where documentation, integrity, and traceability are paramount. Different industries encounter unique challenges while implementing these rigorous tracking mechanisms, requiring innovative approaches to maintain comprehensive and reliable records.
The following table highlights key sectors where chain of custody protocols are critical, grouping them by application to clarify the breadth of industry adoption.
| Sector | Application Focus | Example Activities |
|---|---|---|
| Forensic Investigations | Evidence tracking | Collecting and transferring crime scene items |
| Medical Research | Specimen management | Handling and analysing biological samples |
| Environmental Testing | Sample documentation | Tracking field environmental samples |
| Pharmaceutical Development | Drug trial material tracking | Managing investigational pharmaceuticals |
| Supply Chain Management | Product authenticity | Verifying goods movement and inventory |
| Digital Forensics | Data integrity | Ensuring secure handling of digital evidence |
Diverse Sector Implementation
National Center for Biotechnology Information highlights the extensive application of chain of custody across various critical sectors. From forensic science and legal proceedings to environmental sampling and healthcare, organisations must develop meticulous protocols that ensure absolute transparency and accountability.
Key sectors implementing chain of custody include:
- Forensic Investigations: Tracking physical evidence
- Medical Research: Managing biological specimens
- Environmental Testing: Documenting sample collections
- Pharmaceutical Development: Monitoring drug trial materials
Technological and Procedural Challenges
Implementing robust chain of custody protocols presents significant challenges for organisations. Traditional manual documentation methods are labour-intensive, prone to human error, and increasingly inadequate in complex, fast-moving professional environments. Modern organisations are turning to sophisticated technological solutions like Laboratory Information Management Systems (LIMS) and blockchain technologies to automate and secure tracking processes.
These technological innovations address critical challenges by providing real-time tracking, creating immutable records, and reducing human intervention. Advanced digital platforms enable organisations to create comprehensive audit trails, implement multi-factor authentication, and ensure instantaneous documentation of every single interaction with tracked items.
Ultimately, successful chain of custody implementation requires a strategic blend of technological innovation, comprehensive training, and organisational commitment to maintaining the highest standards of professional integrity and accountability.
Elevate Your Chain of Custody Standards with Secure Courier Solutions
Are you worried about how the integrity of your critical items is maintained from collection to delivery? The article on the importance of chain of custody highlights the risks of poor documentation, insecure handling, and the possible loss of accountability. If your business relies on evidence, time-sensitive documents, or other high-value items needing secure transfer, you cannot afford to leave the chain of custody to chance. BHA Courier gives you peace of mind through meticulous tracking, controlled access, and professional handling at every step, all in line with best practices discussed in the article.
Choose a delivery partner who shares your commitment to transparency and reliability. With guaranteed same-day and next-day services, parcel tracking, and secure handling protocols, BHA Courier protects your chain of custody throughout the UK. Take action now to resolve your chain of custody concerns and experience service designed for organisations that demand more. Visit our homepage to book a secure delivery today.
Frequently Asked Questions
What is chain of custody?
Chain of custody is a documentation and tracking process that ensures the integrity, security, and traceability of evidence, items, or materials from their initial collection to final disposition.
Why is chain of custody important in legal proceedings?
In legal contexts, an unbroken chain of custody is essential for ensuring the admissibility of evidence in court. Any breaks in this chain can potentially compromise the integrity of the legal process.
How does chain of custody apply to digital evidence?
Chain of custody applies to digital evidence by requiring the same rigorous tracking and documentation protocols as with physical items, ensuring data integrity and preventing unauthorized access or alterations.
What challenges do organisations face when implementing chain of custody protocols?
Organisations often face challenges such as labour-intensive manual documentation processes and human errors. To overcome these, they are increasingly using advanced technologies, such as Laboratory Information Management Systems (LIMS) and blockchain, to automate and secure tracking processes.


